Paper:
Fine-Grained Access Control Scheme Based on Improved Proxy Re-Encryption in Cloud
Zhenwu Xu*, Jinan Shen*,†, Fang Liang**, and Yingjie Chen*
*School of Information Engineering, Hubei Minzu University
No.39 Xueyuan Road, Enshi, Hubei 445000, China
**School of Mathematics and Statistics, Hubei Minzu University
No.39 Xueyuan Road, Enshi, Hubei 445000, China
†Corresponding author
Cloud storage technology has attracted a considerable number of users owing to its exponential growth. Storing data in the cloud can save the resources of local storage configuration and reduce the cost of local hardware investment. However, the data stored in the cloud is out of the physical control (out of control) of the user. Based on the service characteristics of the cloud environment and the security requirements of user privacy data in the cloud environment, this paper proposes an improved identity proxy re-encryption algorithm based on the advanced encryption standard algorithm. The performance of the algorithm is optimized by reducing the number of bilinear mapping operations, whose calculation takes the longest time in the proxy re-encryption scheme. Only two bilinear mapping operations are required in this scheme. In addition, the encrypted data are tested to different degrees. The experimental results show that this scheme satisfies encryption and decryption performance requirements of the user.
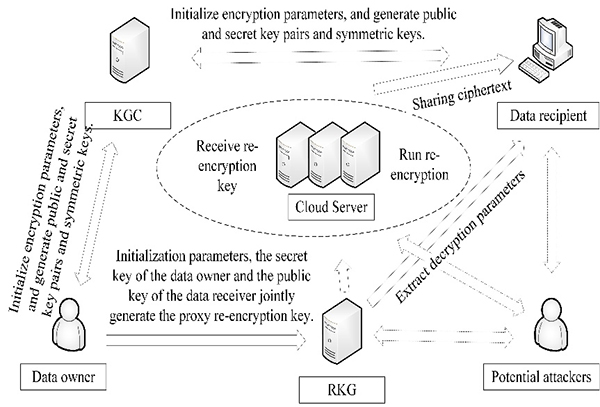
Improved proxy re-encryption algorithm
- [1] Y. Liu, “Image Encryption Algorithm Based on a Hyperchaotic System and Fractional Fourier Transform,” J. Adv. Comput. Intell. Intell. Inform., Vol.23, No.5, pp. 805-809, 2019.
- [2] Z. Xu, J. Shen, P. Luo, and F. Liang, “PVcon: Localizing Hidden Concurrency Errors with Prediction and Verification,” IEEE Access, Vol.8, pp. 165373-165386, 2020.
- [3] M. Armbrust, A. Fox, R. Griffith et al., “A view of cloud computing,” Communications of the ACM, Vol.53, No.4, pp. 50-58, 2010.
- [4] D. E. Bell and L. J. LaPadula, “Secure computer systems: mathematical foundations and model,” Mitre Corporation, 1974.
- [5] A. Shamir, “Identity-based cryptosystems and signature schemes,” Lecture Notes in Computer Science: Workshop on the Theory and Application of Cryptographic Techniques (Crypto 1984), Vol.196, pp. 47-53, 1984.
- [6] C. Delerablée, P. Paillier, and D. Pointcheval, “Fully collusion secure dynamic broadcast encryption with constant-size ciphertexts or decryption keys,” Lecture Notes in Computer Science: Int. Conf. on Pairing-Based Cryptography (Pairing 2007), Vol.4575, pp. 39-59, 2007.
- [7] J. Shen, X. Deng, and Z. Xu, “Multi-security-level cloud storage system based on improved proxy re-encryption,” Eurasip J. on Wireless Communications and Networking, Vol.2019, Article No.277, pp. 1-12, 2019.
- [8] J. Crampton and G. Loizou, “Administrative scope: a foundation for role-based administrative models,” ACM Trans. on Information and System Security, Vol.6, No.2, pp. 201-231, 2003.
- [9] J. Crampton, “Understanding and developing role-based administrative models,” Proc. of the 12th ACM Conf. on Computer and Communications Security, pp. 158-167, 2005.
- [10] L. Zhou, V. Varadharajan, and M. Hitchens, “Enforcing Role-Based Access Control for Secure Data Storage in the Cloud,” The Computer J., Vol.54, No.10, pp. 1675-1687, 2011.
- [11] J. Bethencourt, A. Sahai, and B. Waters, “Ciphertext-policy attribute-based encryption,” IEEE Symp. on Security and Privacy, pp. 321-334, 2007.
- [12] C. Gentry and S. Halevi, “Implementing Gentry’s fully-homomorphic encryption scheme,” Proc. of 30th Annual Int. Conf. on Theory and Applications of Cryptographic Techniques, pp. 129-148, 2019.
- [13] Z. Brakerski and V. Vaikuntanathan, “Efficient fully homomorphic encryption from (standard) LWE,” Proc. of IEEE Symp. on Foundations of Computer Science, pp. 97-106, 2011.
- [14] B. Liu, J. Liu, S. Wang et al., “HEVC Video Encryption Algorithm Based on Integer Dynamic Coupling Tent Mapping,” J. Adv. Comput. Intell. Intell. Inform., Vol.24, No.3, pp. 335-345, 2020.
- [15] A. Haggag, M. Ghoneim, J. Lu et al., “Access Control and Scalable Encryption Using a Stream Cipher for JPEG 2000 Encoded Images,” J. Adv. Comput. Intell. Intell. Inform., Vol.11, No.7, pp. 728-734, 2007.
- [16] J. Hu, J. Shen, and F. Liang, “An improved identity-based broadcast proxy re-encryption storage scheme in cloud,” Application Research of Computers, Vol.34, No.5, pp. 1520-1524, 2017.
- [17] X. Chen and G. Feng, “Direct Anonymous Attestation Based on Bilinear Maps,” J. of Software, Vol.21, No.8, pp. 2070-2078, 2010.
- [18] J. Daemen and V. Rijmen, “The Design of Rijndael: AES – The Advanced Encryption Standard,” Springer, 2002.
- [19] P. Xu, G. Cui, and F. Lei, “An Efficient and Provably Secure IBE Scheme Without Bilinear Map,” J. of Computer Research and Development, Vol.45, No.10, pp. 1687-1695, 2008.
- [20] W. Han, “Analysis of AES encryption algorithm and its security research,” Computer Applications of Petroleum, Vol.16, No.2, pp. 46-48, 2008.
 This article is published under a Creative Commons Attribution-NoDerivatives 4.0 Internationa License.
This article is published under a Creative Commons Attribution-NoDerivatives 4.0 Internationa License.