Research Paper:
Massive Data Connection Architecture Design of Web Platform Based on Blockchain
Hongping Cao*,**, Hongxing Cao***,†, Hongwei Zhou*, Yifeng Wu*, and Siyu Xu*
*School of Data Science, Guangzhou Huashang College
Guangzhou, Guangdong 511300, China
**School of Computer Science, Taylor’s University
Subang Jaya, Selangor 47500, Malaysia
***School of Electrical and Computer Engineering, Guangzhou Nanfang College
Guangzhou, Guangdong 510970, China
†Corresponding author
In order to improve the universality and security of the data management of the Internet of Things and avoid the single point of failure problem in the traditional management architecture, this paper proposes a massive connection management architecture based on blockchain. The blockchain is reconstructed according to the hierarchical structure of blockchain technology, and with reference to the attribute-based access control mechanism, a data exchange model is designed using gossip mode and TLS networking mode to ensure the safe transmission of data. The peer computer network technology, data signature, and consensus mechanism are used to complete the design of the data exchange network layer and realize the design of the blockchain-based massive connection management architecture, so as to effectively avoid the single point of failure problem in the traditional management architecture and greatly reduce the burden of the management center. The access requests of massive devices in 5G application scenarios were simulated, and the results showed that the blockchain-based access control architecture designed in this article can quickly process received requests, with information leakage below 10%, improving the security and processing performance of data connections, achieving efficient processing and management of large-scale data, and providing reliable guarantees for the development of the Internet era.
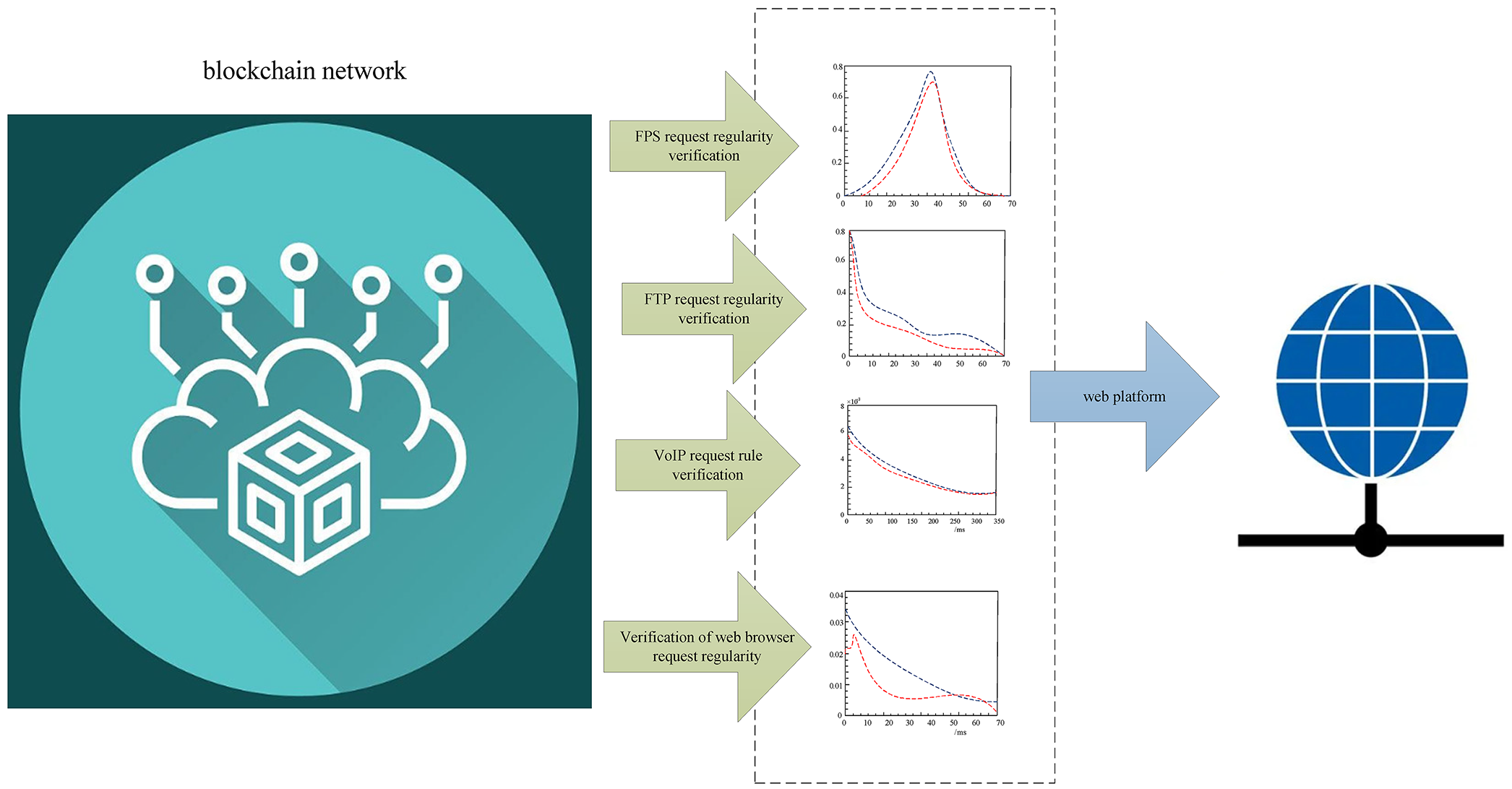
Graphical summary of web platform data connectivity architecture design
- [1] Y. Zhang, D. Zheng, and R. H. Deng, “Security and privacy in smart health: Efficient policy-hiding attribute-based access control,” IEEE Internet of Things J., Vol.5, No.3, pp. 2130-2145, 2018. https://doi.org/10.1109/JIOT.2018.2825289
- [2] Y. Zhang, X. Chen, J. Li, D. S. Wong, H. Li, and I. You, “Ensuring attribute privacy protection and fast decryption for outsourced data security in mobile cloud computing,” Information Sciences, Vol.379, pp. 42-61, 2017. https://doi.org/10.1016/j.ins.2016.04.015
- [3] D. Han, N. Pan, and K.-C. Li, “A traceable and revocable ciphertext-policy attribute-based encryption scheme based on privacy protection,” IEEE Trans. on Dependable and Secure Computing, Vol.19, Issue 1, pp. 316-327, 2020. https://doi.org/10.1109/TDSC.2020.2977646
- [4] Y. Jiang, W. Susilo, Y. Mu, and F. Guo, “Ciphertext-policy attribute-based encryption against key-delegation abuse in fog computing,” Future Generation Computer Systems, Vol.78, No.2, pp. 720-729, 2018. https://doi.org/10.1016/j.future.2017.01.026
- [5] J. Li, Q. Yu, Y. Zhang, and J. Shen, “Key-policy attribute-based encryption against continual auxiliary input leakage,” Information Sciences, Vol.470, pp. 175-188, 2019. https://doi.org/10.1016/j.ins.2018.07.077
- [6] P. Ruan, T. T. A. Dinh, Q. Lin, M. Zhang, G. Chen, and B. C. Ooi, “LineageChain: A fine-grained, secure and efficient data provenance system for blockchains,” The VLDB J., Vol.30, No.1, pp. 3-24, 2021. https://doi.org/10.1007/s00778-020-00646-1
- [7] M. El-Hindi, C. Binnig, A. Arasu, D. Kossmann, and R. Ramamurthy, “BlockchainDB: A shared database on blockchains,” Proc. of the VLDB Endowment, Vol.12, No.11, pp. 1597-1609, 2019. https://doi.org/10.14778/3342263.3342636
- [8] Y. Peng, M. Du, F. Li, R. Cheng, and D. Song, “FalconDB: Blockchain-based collaborative database,” Proc. of the 2020 ACM SIGMOD Int. Conf. on Management of Data, pp. 637-652, 2020. https://doi.org/10.1145/3318464.3380594
- [9] C. Zhang, C. Xu, J. Xu, Y. Tang, and B. Choi, “GEM2-Tree: A Gas-Efficient Structure for Authenticated Range Queries in Blockchain,” 35th IEEE Int. Conf. on Data Engineering (ICDE’19), 2019. https://doi.org/10.1109/ICDE.2019.00080
- [10] S. Wang, T. T. A. Dinh, Q. Lin, Z. Xie, M. Zhang, Q. Cai, G. Chen, W. Fu, B. C. Ooi, and P. Ruan, “ForkBase: An Efficient Storage Engine for Blockchain and Forkable Applications,” arXiv:1802.04949, 2018. https://doi.org/10.48550/arXiv.1802.04949
- [11] D. Jia, J. Xin, Z. Wang, W. Guo, and G. Wang, “ElasticChain: Support Very Large Blockchain by Reducing Data Redundancy,” Asia-Pacific Web (APWeb) and Web-Age Information Management (WAIM) Joint Int. Conf. on Web and Big Data, Springer, pp. 440-454, 2018. https://doi.org/10.1007/978-3-319-96893-3_33
- [12] J. Lind, O. Naor, I. Eyal, F. Kelbert, P. Pietzuch, and E. G. Sirer, “Teechain: Reducing storage costs on the blockchain with offline payment channels,” Proc. of the 11th ACM Int. Systems and Storage Conf., p. 125, 2018. https://doi.org/10.1145/3211890.3211904
- [13] Z. Ma, L. Wang, X. Wang, Z. Wang, and W. Zhao, “Blockchain-Enabled Decentralized Trust Management and Secure Usage Control of IoT Big Data,” IEEE Internet of Things J., Vol.7, No.5, pp. 4000-4015, 2019. https://doi.org/10.1109/JIOT.2019.2960526
- [14] K. Karlsson, W. Jiang, S. Wicker, D. Adams, E. Ma, R. van Renesse, and H. Weatherspoon, “Vegvisir: A Partition-Tolerant Blockchain for the Internet-of-Things,” 2018 IEEE 38th Int. Conf. on Distributed Computing Systems (ICDCS), pp. 1150-1158, 2018. https://doi.org/10.1109/ICDCS.2018.00114
- [15] A. Alnoman, S. K. Sharma, W. Ejaz, and A. Anpalagan, “Emerging Edge Computing Technologies for Distributed IoT Systems,” IEEE Network, Vol.33, No.6, pp. 140-147, 2019. https://doi.org/10.1109/MNET.2019.1800543
- [16] J. Sun, H. Xiong, X. Liu, Y. Zhang, X. Nie, and R. H. Deng, “Lightweight and Privacy-Aware Fine-Grained Access Control for IoT-Oriented Smart Health,” IEEE Internet of Things J., Vol.7, No.7, pp. 6566-6575, 2020. https://doi.org/10.1109/JIOT.2020.2974257
- [17] S. F. Aghili, H. Mala, M. Shojafar, and P. Peris-Lopez, “LACO: Lightweight Three-Factor Authentication, Access Control and Ownership Transfer Scheme for E-Health Systems in IoT,” Future Generation Computer Systems, Vol.96, No.7, pp. 410-424, 2019. https://doi.org/10.1016/j.future.2019.02.020
- [18] M. Aman, U. Javaid, and B. Sikdar, “A Privacy-Preserving and Scalable Authentication Protocol for the Internet of Vehicles,” IEEE Internet of Things J., Vol.8, No.2, pp. 1123-1139, 2020. https://doi.org/10.1109/JIOT.2020.3010893
- [19] S. F. Aghili, H. Mala, P. Kaliyar, and M. Conti, “SecLAP: Secure and lightweight RFID authentication protocol for medical IoT,” Future Generation Computer Systems, Vol.101, pp. 621-634, 2019. https://doi.org/10.1016/j.future.2019.07.004
- [20] S. Xia, F. Lin, Z. Chen, C. Tang, Y. Ma, and X. Yu, “A Bayesian Game Based Vehicle-to-Vehicle Electricity Trading Scheme for Blockchain-Enabled Internet of Vehicles,” IEEE Trans. on Vehicular Technology, Vol.69, No.7, pp. 6856-6868, 2020. https://doi.org/10.1109/TVT.2020.2990443
- [21] V. Hassija, V. Chamola, V. Saxena, D. Jain, P. Goyal, and B. Sikdar, “A Survey on IoT Security: Application Areas, Security Threats, and Solution Architectures,” IEEE Access, Vol.7, pp. 82721-82743, 2019. https://doi.org/10.1109/ACCESS.2019.2924045
- [22] H. Dai, Z. Zheng, and Y. Zhang, “Blockchain for Internet of Things: A Survey,” IEEE Internet of Things J., Vol.6, No.5, pp. 8076-8094, 2019. https://doi.org/10.1109/JIOT.2019.2920987
- [23] L. Barbierato, A. Estebsari, E. Pons, M. Pau, F. Salassa, M. Ghirardi, and E. Patti, “A Distributed IoT Infrastructure to Test and Deploy Real-Time Demand Response in Smart Grids,” IEEE Internet of Things J., Vol.6, No.1, pp. 1136-1146, 2019. https://doi.org/10.1109/JIOT.2018.2867511
- [24] S. Wang, A. F. Taha, J. Wang, K. Kvaternik, and A. Hahn, “Energy Crowdsourcing and Peer-to-Peer Energy Trading in Blockchain-Enabled Smart Grids,” IEEE Trans. on Systems, Man and Cybernetics, Vol.49, No.8, pp. 1612-1623, 2019. https://doi.org/10.1109/TSMC.2019.2916565
- [25] T.-M. Choi, “Financing Product Development Projects in the Blockchain Era: Initial Coin Offerings Versus Traditional Bank Loans,” IEEE Trans. on Engineering Management, Vol.69, Issue 6, pp. 3184-3196, 2022. https://doi.org/10.1109/TEM.2020.3032426
 This article is published under a Creative Commons Attribution-NoDerivatives 4.0 Internationa License.
This article is published under a Creative Commons Attribution-NoDerivatives 4.0 Internationa License.