Paper:
An ERP Experimental Study About the Effect of Authorization Cue Characteristics on the Privacy Behavior of Recommended Users
Rui Sun, Jia Rong Chen, Yi Xiang Wang, Ying Rui Zhou†, and Ying Yu Luo
Business School, Hua Qiao University
No.269 Chenghua North Road, Fengze District, Quanzhou, Fujian 362021, China
†Corresponding author
At the present time, consumers often disclose their privacy when using online platforms to receive personalized recommendation information and services, but they are also highly concerned whether their privacy is being violated. “Privacy paradox” is becoming a hot topic of research. What are the potential impacts of individual cognitive differences and situational cues on privacy decision-making? How to balance the internal causes of the “privacy paradox” so that consumers are more willing to accept personalized recommendation services based on users’ privacy data? Can the transparency of privacy rights ease user conflict perceptions and promote disclosure intentions? These questions are inconclusive. Therefore, the purpose of this our research was to explore consumer privacy paradoxical behaviors from a novel perspective of the characteristics of authorization cues, and to clarify the internal relationship between individual cognitive processing and privacy authorization cues. This study suggests that the big data platform, when collecting or using user information, should try to reduce the behaviors that induce users’ resistance. It also provides a reference for how to better achieve benign interaction in personalized recommendation between Internet companies and users. The event-related potential technique is adopted to explore the matching relationship between individual cognitive processing and privacy authorization cues and to analyze the internal neural mechanism of the personalized recommendation user in the authorization decision. The experiment simulated the privacy authorization situation, and adopted a 2 × 2 × 2 hybrid experimental design: authority sensitivity (high/low) * authorization transparency (with/without permission) * cognitive style (field dependent/field independent). The experimental results show that: (1) Authorization transparency, authority sensitivity and their interactions will affect the user’s privacy authorization behaviors, and the interaction of the two cues has a greater impact on the behavior than the role of a single cue; (2) The cognitive style will affect the individual’s attention resource allocation in the authorization scenario, which, limited by cognitive resources, will result in selective attention to contextual cues: Compared with the field-independent group with self-characterization as a reference, the field-dependent group induced a greater P2 amplitude; (3) When the two-cue valences in the authoritative scenario are inconsistent, the amplitude of the N2 component is greater than that when the valences are consistent, and the amplitude of the N2 induced by the field-dependent group is more affected by the scenario cue valence; (4) Regardless of whether it is a field-dependent group or a field-independent group, there is no salient difference in the amplitude of LPP components induced in each scenario. According to the results of this study, even if privacy authorization involves high risks, individuals tend to selectively seek supportive cues or avoid obtaining information that is inconsistent with their cognition. This research reveals the differences of neural mechanisms in users’ actual decision-making, provides the possibility for further exploration of the black box behind users’ attitudes and behaviors, and opens up new ideas for the study of the “privacy paradox.”
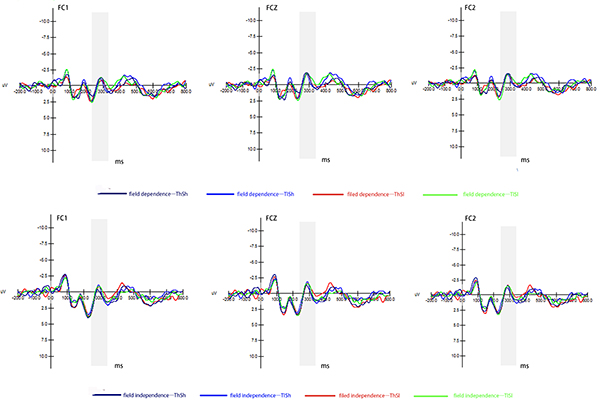
Intra-group comparison of N2 amplitude of field-independent/field-dependent group under various situations
- [1] S. Thirumalai and K. Sinha, “To Personalize or Not to Personalize Online Purchase Interactions: Implications of Self-Selection by Retailers,” Information Systems Research, Vol.24, No.3, pp. 683-708, 2013.
- [2] S. Karwatzki, O. Dytynko, M. Trenz, and D. Veit, “Beyond the Personalization–Privacy Paradox: Privacy Valuation, Transparency Features, and Service Personalization,” J. of Management Information Systems, Vol.34, Issue 2, pp. 369-400, 2017.
- [3] G. Wang, L. Wang, and H. Liu, “Study progress of privacy protection techniques used in personalized recommendation system,” Application Research of Computers, Vol.29, No.6, pp. 2001-2008, 2012 (in Chinese).
- [4] N. Gerber, P. Gerber, and M. Volkamer, “Explaining the privacy paradox: A systematic review of literature investigating privacy attitude and behavior,” Computers & Security, Vol.77, pp. 226-261, 2018.
- [5] R. J. Martis, U. R. Acharya, and H. Adeli, “Current methods in electrocardiogram characterization,” Computers in Biology and Medicine, Vol.48, pp. 133-149, 2014.
- [6] H. Li, J. Wu, Y. Gao, and Y. Shi, “Examining individuals’ adoption of healthcare wearable devices: An empirical study from privacy calculus perspective,” Int. J. of Medical Informatics, Vol.88, pp. 8-17, 2016.
- [7] M. V. Wottrich, E. A. van Reijmersdal, and E. G. Smit, “The privacy trade-off for mobile app downloads: The roles of app value, intrusiveness, and privacy concerns,” Decision Support Systems, Vol.106, pp. 44-52, 2018.
- [8] A. Wei, Q. Liu, and L. Zhang, “Review on Diversity in Personalized Recommender Systems,” Library and Information Service, Vol.57, No.20, pp. 127-135, 2013 (in Chinese).
- [9] A. Kalaï, A. Wafa, C. A. Zayani, and I. Amous, “LoTrust: A social Trust Level model based on time-aware social interactions and interests similarity,” Proc. of the 2016 14th Annual Conf. on Privacy, Security and Trust (PST), pp. 428-436, 2016.
- [10] R. Slavin et al., “Toward a Framework for Detecting Privacy Policy Violations in Android Application Code,” Proc. of the 2016 IEEE/ACM 38th Int. Conf. on Software Engineering (ICSE), pp. 25-36, 2016.
- [11] L. Yu et al., “Toward Automatically Generating Privacy Policy for Android Apps,” IEEE Trans. on Information Forensics and Security, Vol.12, No.4, pp. 865-880, 2017.
- [12] S. Tang, “Based on the Enterprise Network Information Platform Construction and its Authority Mechanism Establishment,” Computer Security, Vol.2012, No.2, pp. 59-61, 2012 (in Chinese).
- [13] K. Rider, “The privacy paradox: how market privacy facilitates government surveillance,” Information, Communication & Society, Vol.21, Issue 10, pp. 1369-1385, 2018.
- [14] N. Lee and O. Kwon, “A privacy-aware feature selection method for solving the personalization–privacy paradox in mobile wellness healthcare services,” Expert Systems with Applications, Vol.42, Issue 5, pp. 2764-2771, 2015.
- [15] C. Flender and G. Müller, “Type Indeterminacy in Privacy Decisions: The Privacy Paradox Revisited,” J. R. Busemeyer et al. (Eds.), “Quantum Interaction: 6th Int. Symp., QI 2012, Paris, France, June 2012, Revised Selected Papers,” pp. 148-159, Springer, 2012.
- [16] J. Xu, W. Zhang, and L. Li, “Journalism and Communication Studies on the Infringement of the right to Internet Privacy in the context of SNSs in Western Countries,” Chinese J. of Journalism & Communication, Vol.36, No.10, pp. 146-158, 2014 (in Chinese).
- [17] H. J. Smith, S. J. Milberg, and S. J. Burke, “Information Privacy: Measuring Individuals’ Concerns about Organizational Practices,” MIS Quarterly, Vol.20, No.2, pp. 167-196, 1996.
- [18] X. Wang and G. Deng, “Daily “Privacy” Practice in the Internet: A Qualitative Research Based on Youth Groups,” China Youth Study, Vol.2018, No.12, pp. 51-56+80, 2018 (in Chinese).
- [19] H. Wang and K. Qin, “Research on Internet Users’ Personal Information Sensitivity,” J. of Intelligence, Vol.31, No.12, pp. 171-175, 2012 (in Chinese).
- [20] C. Lin, Z. Yang, and X. Huang (Eds.), “The Comprehensive Dictionary of Psychology,” Shanghai Educational Publishing House, 2003 (in Chinese).
- [21] R. J. Riding and F. Pearson, “The Relationship between Cognitive Style and Intelligence,” Educational Psychology: An Int. J. of Experimental Educational Psychology, Vol.14, Issue 4, pp. 413-425, 1994.
- [22] D. Maheswaran and S. Chaiken, “Promoting systematic processing in low-motivation settings: Effect of incongruent information on processing and judgment,” J. of Personality and Social Psychology, Vol.61, No.1, pp. 13-25, 1991.
- [23] R. M. Hogarth and N. Karelaia, “Heuristic and Linear Models of Judgment: Matching rules and environments,” Psychological Review, Vol.114, No.3, pp. 733-758, 2007.
- [24] C.-L. Hsu and J. C.-C. Lin, “An empirical examination of consumer adoption of Internet of Things services: Network externalities and concern for information privacy perspectives,” Computers in Human Behavior, Vol.62, pp. 516-527, 2016.
- [25] S. Y. Ho, “Opportunities and challenges of mobile personalization: An exploratory study,” Proc. of the 17th European Conf. on Information Systems (ECIS 2009), pp. 1211-1222, 2009.
- [26] H. Treiblmaier and I. Pollach, “Users’ Perceptions of Benefits and Costs of Personalization,” Proc. of the Int. Conf. on Information Systems (ICIS 2007), Article No.141, 2007.
- [27] H. Zhu et al., “Research on Information Privacy Boundaries and Sensitivity of Net Users,” J. of Guangdong University of Technology, Vol.30, No.4, pp. 26-32, 2013 (in Chinese).
- [28] S. Karwatzki, M. Trenz, V. K. Tuunainen, and D. Veit, “Adverse consequences of access to individuals’ information: an analysis of perceptions and the scope of organisational influence,” European J. of Information Systems, Vol.26, No.6, pp. 688-715, 2017.
- [29] A. D. Miyazaki, D. Grewal, and R. C. Goodstein, “The Effect of Multiple Extrinsic Cues on Quality Perceptions: A Matter of Consistency,” J. of Consumer Research, Vol.32, Issue 1, pp. 146-153, 2005.
- [30] S. Campanella et al., “Why cognitive event-related potentials (ERPs) should have a role in the management of alcohol disorders,” Neuroscience & Biobehavioral Reviews, Vol.106, pp. 234-244, 2019.
- [31] L. Carretié, F. Mercado, M. Tapia, and J. A. Hinojosa, “Emotion, attention, and the ‘negativity bias’, studied through event-related potentials,” Int. J. of Psychophysiology, Vol.41, Issue 1, pp. 75-85, 2001.
- [32] P. J. Lang, M. M. Bradley, and B. N. Cuthbert, “ Motivated Attention: Affect, Activation, and Action,” P. J. Lang, R. F. Simons, and M. Balaban (Eds.), “Attention and Orienting: Sensory and Motivational Processes,” pp. 97-136, Lawrence Erlbaum Associates, Inc., 1997.
- [33] B. N. Cuthbert et al., “Brain potentials in affective picture processing: covariation with autonomic arousal and affective report,” Biological Psychology, Vol.52, Issue 2, pp. 95-111, 2000.
- [34] H. Treiblmaier, M. Madlberger, N. Knotzer, and I. Pollach, “Evaluating personalization and customization from an ethical point of view: an empirical study,” Proc. of the 37th Annual Hawaii Int. Conf. on System Sciences, 10pp., 2004.
- [35] H. J. Smith, T. Dinev, and H. Xu, “Information privacy research: an interdisciplinary review,” MIS Quarterly, Vol.35, No.4, pp. 989-1016, 2011.
- [36] J. Lu et al., “A web-based personalized business partner recommendation system using fuzzy semantic techniques,” Computational Intelligence, Vol.29, Issue 1, pp. 37-69, 2013.
- [37] T. Dinev, H. Xu, J. H. Smith, and P. Hart, “Information privacy and correlates: an empirical attempt to bridge and distinguish privacy-related concepts,” European J. of Information Systems, Vol.22, Issue 3, pp. 295-316, 2013.
- [38] J. C. Zimmer et al., “Knowing your customers: Using a reciprocal relationship to enhance voluntary information disclosure,” Decision Support Systems, Vol.48, Issue 2, pp. 395-406, 2010.
 This article is published under a Creative Commons Attribution-NoDerivatives 4.0 Internationa License.
This article is published under a Creative Commons Attribution-NoDerivatives 4.0 Internationa License.