Short Paper:
Image Encryption Algorithm Based on a Hyperchaotic System and Fractional Fourier Transform
Yang Liu
College of Information and Electronic Engineering, Hunan City University
Yiyang, Hunan 413000, China
An image encryption scheme that combines a hyperchaotic system with standard weighted fractional Fourier transform theory is proposed. Simulation results showed that grayscale distribution of the encrypted image was balanced, correlation coefficients of adjacent pixels were highly irrelevant, and the encrypted image was highly sensitive to the secret key, offering good robustness against attacks and a larger key space.
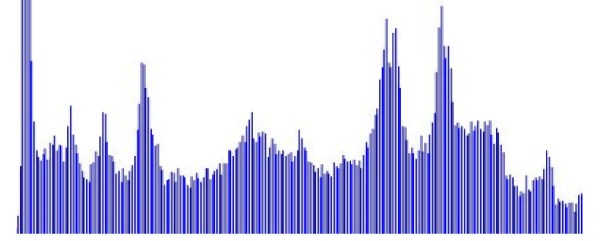
The encrypted grayscale histogram
- [1] X.-Y. Wang, L. Yang, R. Liu, and A. Kadir, “A chaotic image encryption algorithm based on perceptron model,” Nonlinear Dynamics, Vol.62, Issue 3, pp. 615-621, 2010.
- [2] Y. Zhou, L. Bao, and C. L. P. Chen, “A new 1D chaotic system for image encryption,” Signal Processing, Vol.97, pp. 172-182, 2014.
- [3] X. Wang and H.-L. Zhang, “A novel image encryption algorithm based on genetic recombination and hyper-chaotic systems,” Nonlinear Dynamics, Vol.83, Issue 1-2, pp. 333-346, 2016.
- [4] Y.-Q. Zhang and X.-Y. Wang, “A new image encryption algorithm based on non-adjacent coupled map lattices,” Applied Soft Computing, Vol.26, pp. 10-20, 2015.
- [5] X. Wang, C. Liu, D. Xu, and C. Liu, “Image encryption scheme using chaos and simulated annealing algorithm,” Nonlinear Dynamics, Vol.84, Issue 3, pp. 1417-1429, 2016.
- [6] M. J. Rostami, S. Saryazdi, H. Nezamabadi-pour, and A. Shahba, “Chaos-Based Image Encryption Using Sum Operation Modulo 4 and 256,” IETE J. Research, Vol.62, Issue 2, pp. 179-188, 2016.
- [7] H. Khanzadi, M. Eshghi, and S. E. Borujeni, “Design and FPGA Implementation of a Pseudo Random Bit Generator Using Chaotic Maps,” IETE J. Res., Vol.59, Issue 1, pp. 63-73, 2013.
- [8] D. Coppersmith, “The Data Encryption Standard (DES) and its strength against attacks,” IBM J. of Research Development, Vol.38, Issue 3, pp. 243-250, 1994.
- [9] H. Williams, “A modification of the RSA public-key encryption procedure,” IEEE Trans. on Information Theory, Vol.26, Issue 6, pp. 726-729, 1980.
- [10] Y.-Q. Zhang and X.-Y. Wang, “Analysis and improvement of a chaos-based symmetric image encryption scheme using a bit-level permutation,” Nonlinear Dynamics, Vol.77, Issue 3, pp. 687-698, 2014.
 This article is published under a Creative Commons Attribution-NoDerivatives 4.0 Internationa License.
This article is published under a Creative Commons Attribution-NoDerivatives 4.0 Internationa License.