Paper:
Anomaly Detection Algorithm Based on CFSFDP
Weiwu Ren*, Jianfei Zhang*, Xiaoqiang Di*, Yinan Lu**, Bochen Zhang**, and Jianping Zhao*
*School of Computer Science and Technology, Changchun University of Science and Technology
No.7089 Weixing Road, Changchun, Jilin 130022, China
**College of Computer Science and Technology, Jilin University
No.2699 Qianjin Street, Changchun, Jilin 130012, China
Clustering by fast search and find of density peak (CFSFDP) is a simple and crisp density-clustering algorithm. The original algorithm is not suitable for direct application to anomaly detection. Its clustering results have a high level of redundant density information. If used directly as behavior profiles, the computation and storage costs of anomaly detection are high. Therefore, an improved algorithm based on CFSFDP is proposed for anomaly detection. The improved algorithm uses a few data points and their radius to support behavior profiles, and deletes the redundant data points without supporting profiles. This method not only reduces the large amount of data storage and distance calculation in the process of generating profiles, but also reduces the search space of profiles in the detection process. Numerous experiments show that the improved algorithm generates profiles faster than density-based spatial clustering of application with noise (DBSCAN), and has better profile precision than adaptive real-time anomaly detection with incremental clustering (ADWICE). The improved algorithm inherits the arbitrary shape clusters of CFSFDP, and improves the storage and computation performance. Compared with DBSCAN and ADWICE, the improved anomaly-detection algorithm based on CFSFDP has more balanced detection precision and real-time performance.
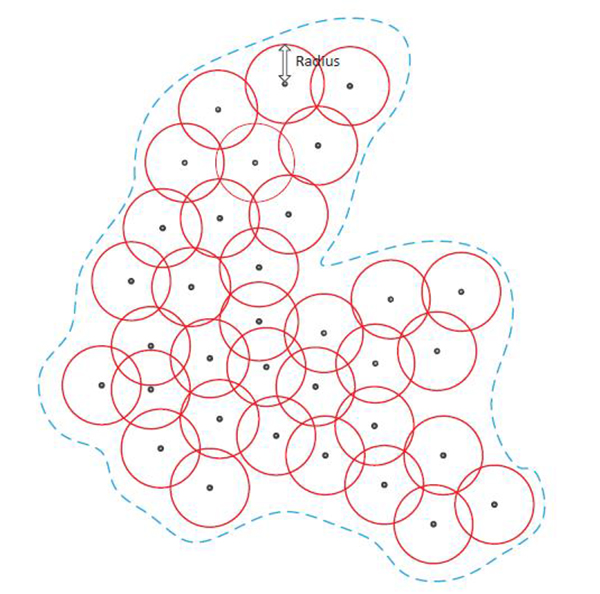
The profiles supported by the center point and its radius
- [1] H. Bäcklund, A. Hedblom, and N. Neijman, “DBSCAN: A density-based spatial clustering of application with noise,” Linköpings Universitet–ITN, Data Mining TNM033, 2011.
- [2] S. Shamshirband, A. Amini, N. B. Anuar, M. L. M. Kiah, W. T. Ying, and S. Furnell, “D-FICCA: A density-based fuzzy imperialist competitive clustering algorithm for intrusion detection in wireless sensor networks,” Measurement, Vol. 55, pp. 212-226, 2014.
- [3] T. Zhang, R. Ramakrishnan, and M. Livny, “BIRCH: an efficient data clustering method for very large databases,” Proc. of the 1996 ACM SIGMOD Int. Conf. on Management of Data, pp. 103-114, 1996.
- [4] K. Burbeck and S. Nadjm-Tehrani, “Adaptive real-time anomaly detection with incremental clustering,” Information Security Technical Report, Vol.12, Issue 1, pp. 56-67, 2007.
- [5] S. Garg and S. Batra, “A novel ensembled technique for anomaly detection,” Int. J. of Communication Systems, Vol.30, Issue 11, Article No.e3248, 2017.
- [6] Y. Gu, Y. Wang, Z. Yang, F. Xiong, and Y. Gao, “Multiple-Features-Based Semisupervised Clustering DDoS Detection Method,” Mathematical Problems in Engineering, Vol.2017, doi: 10.1155/2017/5202836, 2017.
- [7] B. Harish and S. A. Kumar, “Anomaly based intrusion detection using modified fuzzy clustering,” Int. J. of Interactive Multimedia and Artificial Intelligence, Vol.4, No.6, pp. 54-59, 2017.
- [8] J. Zou, D. Tao, and J. Yu, “A Hybrid Intrusion Detection Model for Web Log-Based Attacks,” J. of Internet Technology, Vol.18, No.4, pp. 887-895, 2017.
- [9] J. Dromard, G. Roudière, and P. Owezarski, “Online and Scalable Unsupervised Network Anomaly Detection Method,” IEEE Trans. on Network and Service Management, Vol.14, Issue 1, pp. 34-47, 2017.
- [10] J. Karimpour, S. Lotfi, and A. T. Siahmarzkooh, “Intrusion detection in network flows based on an optimized clustering criterion,” Turkish J. of Electrical Engineering & Computer Sciences, Vol.25, pp. 1963-1975, 2017.
- [11] S. H. Oh and W. S. Lee, “An anomaly intrusion detection method by clustering normal user behavior,” Computers & Security, Vol.22, Issue 7, pp. 596-612, 2003.
- [12] A. Rodriguez and A. Laio, “Clustering by fast search and find of density peaks,” Science, Vol.344, Issue 6191, pp. 1492-1496, 2014.
- [13] Y. Zhou and X. Jiang, “Dissecting Android Malware: Characterization and Evolution,” Proc. of 2012 IEEE Symp. on Security and Privacy, pp. 95-109, 2012.
- [14] K. Fans, “Virus sample data area,” https://bbs.kafan.cn/thread-1671514-1-1.html [accessed May 24, 2018]
- [15] I. Burguera, U. Zurutuza, and S. Nadjm-Tehrani, “Crowdroid: behavior-based malware detection system for android,” Proc. of the 1st ACM Workshop on Security and Privacy in Smartphones and Mobile Devices, pp. 15-26, 2011.
- [16] A. Reina, A. Fattori, and L. Cavallaro, “A system call-centric analysis and stimulation technique to automatically reconstruct android malware behaviors,” 2013 European Workshop on Systems Security (EuroSec), 2013.
- [17] A. Shabtai, U. Kanonov, Y. Elovici, C. Glezer, and Y. Weiss, “Andromaly: a behavioral malware detection framework for android devices,” J. of Intelligent Information Systems, Vol.38, pp. 161-190, doi: 10.1007/s10844-010-0148-x, 2012.
 This article is published under a Creative Commons Attribution-NoDerivatives 4.0 Internationa License.
This article is published under a Creative Commons Attribution-NoDerivatives 4.0 Internationa License.